What is data authorization?
As organizations handle growing volumes of sensitive data, ensuring precise, policy-driven access control is important. Data authorization provides fine-grained access control, determining not just who can access data, but what specific data they can see or modify—down to individual records, fields, or attributes.
We’ll explore why data authorization matters, and how organizations can implement it to reduce risk, meet compliance requirements, and enhance user experience.
Defining data authorization
Data authorization refers to the enforcement of fine-grained access policies that dictate precisely which data users, applications, or AI agents can access within a system. Unlike traditional role-based access control (RBAC), which grants broad permissions based on static roles, data authorization uses contextual, attribute-based policies to enforce real-time, granular access decisions.
For example, rather than giving a user access to an entire database table, data authorization can restrict access based on attributes such as department, region, or data sensitivity. This ensures that each access decision is made dynamically, based on policy rules aligned with security and business requirements.
Why data authorization matters
Security is the most obvious reason to implement data authorization. Limiting data access to only what’s necessary greatly reduces the risk of data breaches or misuse. If an account is compromised or an insider attempts improper access, fine-grained authorization policies can contain the damage by ensuring the user still cannot see data beyond their scope. Without these controls, the risk of unauthorized access to sensitive information skyrockets, exposing businesses to consequences like data breaches. By enforcing the principle of least privilege (each user gets only the access they need), organizations can strengthen their security.
Compliance is another major driver. Industries under strict regulations – healthcare, finance, government, and others – are often required by law to enforce granular access controls on sensitive data. For example, healthcare providers need to abide by HIPAA rules to safeguard patient health information. Data authorization policies can ensure that, say, a doctor or nurse can view a patient’s medical records only if they are directly involved in that patient’s care (and deny access otherwise). In fact, fine-grained controls are quite important for meeting privacy mandates. They allow businesses to align access rules with regulations like GDPR (for personal data protection), HIPAA (health data privacy), and PCI-DSS (payment card security). Proper data authorization therefore helps avoid costly violations by making sure that sensitive data is only accessible to authorized personnel under the right conditions, with thorough audit logs to prove it.
Finally, user experience and business agility benefit from good data authorization. Sharing data across teams, services, or even with third parties seamlessly is a necessity, but needs to be done in a safe manner. If authorization is too locked-down (for fear of breaches), it can hinder productivity and data insights; if it’s too permissive, it creates security holes. Fine-grained data authorization strikes a balance. It enables frictionless access for legitimate users while keeping data safe from everyone else. In other words, when done right, you don’t have to choose between security and usability. By making authorization decisions context-aware and automated, developers can build features that leverage data (for example, personalized analytics or cross-department collaboration) without constantly worrying about manual permission tweaks. This improves confidence in data sharing and overall user trust, since each user knows they’ll only see what they are meant to see – no more, no less.
Implementing data authorization
The goal here is to externalize and centralize the authorization logic rather than sprinkling ad-hoc checks throughout code. In practice, this often means using a policy-based authorization service or library that evaluates access rules at runtime. Instead of hardcoding who can access which data in dozens of places, the application can ask a single authority “Is this user allowed to do this action on this data?” and act based on the answer. This simplifies development, and makes it easier to review and update access rules in one place.
A recommended approach is to use a Policy Decision Point (PDP) – a dedicated service that takes in the relevant context (the user’s identity and attributes, the action being attempted, details of the data/resource in question) and returns an ALLOW or DENY decision. The Cerbos authorization solution follows this model. You define your access policies in a declarative way (often in configuration files or a UI), and at runtime the application queries the engine for each decision. For example, Cerbos lets you offload authorization logic to a stateless service with a simple API: your app provides information about the principal (user or service), the action, and the resource they want to access, and Cerbos responds with ALLOW or DENY based on the policies in effect.
This decoupling means you can change policies without changing application code, and you can have consistent enforcement across many services.
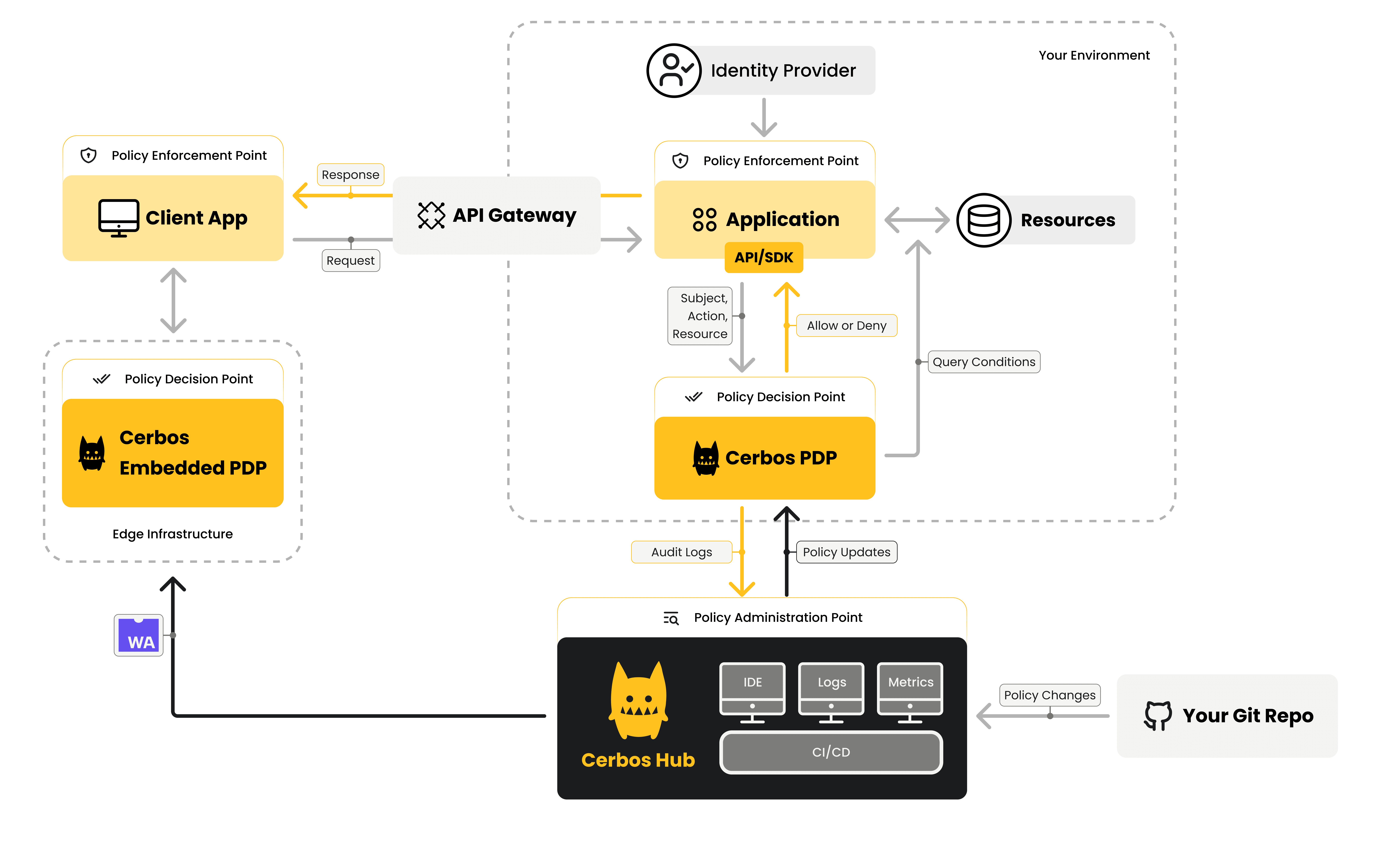
In the diagram above, the application acts as a Policy Enforcement Point (PEP) in front of the data. When a user makes a request (for example, to view a certain record), the application sends the user’s Subject details, the intended Action, and the Resource info to the Cerbos PDP via an API/SDK. The PDP then evaluates this request against the defined policies and returns an ALLOW or DENY decision. The decision accounts for rules that administrators or developers have configured – for instance, “User must have role X and the record’s region attribute must match the user’s region to allow view.” If the policy conditions are met, the PDP grants access; otherwise it denies. By handling authorization as a focused service, the application code stays simpler (it just asks and obeys the answer), and policy changes (like adding a new rule or role) can be made centrally and take effect immediately across all uses of the service.
To illustrate, imagine we have a business rule: “Sales managers can only view sales data for their own region.” In a policy-based system like Cerbos, this rule can be written as a policy (rather than scattered if statements). For example, you might define a rule stating that a principal with role sales_manager can perform the view action on a sales record resource only if resource.attr.region == principal.attr.region. With that policy in place, whenever a sales manager attempts to view a sales record, the PDP will automatically check the record’s region against the manager’s region attribute and allow or deny accordingly. The application simply gets the answer and, if denied, can inform the user that they don’t have access to that particular data. This kind of attribute-based filtering is a hallmark of data authorization in practice – enforcing business-specific constraints on which data a given user is permitted to see.
Where this becomes more of a challenge is when a system needs to list all the records a user has access to. The anti-pattern for this would be to fetch every record from the database and then check them one by one for whether access should be allowed. This is terrible for performance as you could be retrieving thousands, or millions of records just for the result to be that the user doesn’t have access to any of them.
The best way to fit this requirement is to use a PDP that supports partial evaluation of policies and can return a query filter derived from the currently live policies. This query plan contains all the conditions that need to be met on a record for the current user to be allowed access - think of it like getting back the WHERE clause in a SQL query. This in essence pushes down the predicates into the database query itself ensuring only the records a user has access to are returned. Cerbos PDP supports this out of the box via its PlanResources API and returns a store-agnostic Query Plan which can be adapted into whichever data layer you are using. Reference adapters are available for Prisma, Mongoose, and SQLAlchemy.
Another benefit of using a dedicated authorization service is easier auditing and updates. Because all decisions funnel through one point, you can log every access decision and review who accessed what data. If requirements change (say, a new privacy law or a new user role is introduced), you update the policy in one place and all application flows immediately adopt it.
In summary, implementing data authorization in practice often means adopting a policy engine like Cerbos to handle the heavy lifting of decision-making, using declarative policies to define the rules, and integrating that engine with your application’s requests. This results in clearer, more maintainable code and a much stronger security posture.
Conclusion
Data authorization is about enforcing the right access at the right time. It complements authentication by adding brains to the brawn: once we know who the user is, we still ask if they should have access to this particular piece of data? By building this questioning attitude into our systems, we create applications that are not only secure and compliant by design, but also more trustworthy and user-friendly.
Adopting such a system is now a best practice and, increasingly, a necessity for any organization serious about security and privacy. As you design or refactor your applications, treating data authorization as a first-class concern will pay off in more maintainable code, easier compliance, and peace of mind that your “crown jewels” are well protected even as you continue to leverage them for innovation.
If you’re interested in implementing externalized authorization - try out Cerbos Hub or book a call with a Cerbos engineer to see how our solution can help streamline access control in your applications.
FAQ
Book a free Policy Workshop to discuss your requirements and get your first policy written by the Cerbos team
Related Articles
Subscribe to our newsletter
Join thousands of developers | Features and updates | 1x per month | No spam, just goodies.






