Strategies for securing Non-Human Identities
“How can I secure non-human identities in my tech stack?” It’s one of the most common questions we hear from Cerbos customers in 2025. Teams usually have strong controls for employees and customers as part of their IAM programs.
But many companies still over-privilege and implicitly trust their NHIs. As services, workloads, and AI agents spread across systems, this blind trust is becoming a major problem. We keep hearing the same thing: machines and workloads need the same level of security as human users.
On a recent call, a company we work with shared something that really stood out. They have 1.5 million customers, 40,000 partners, 2,500 internal users, and more than 4,500 services and workloads. Yet they admitted they had no real visibility into what those services were doing on behalf of their users.
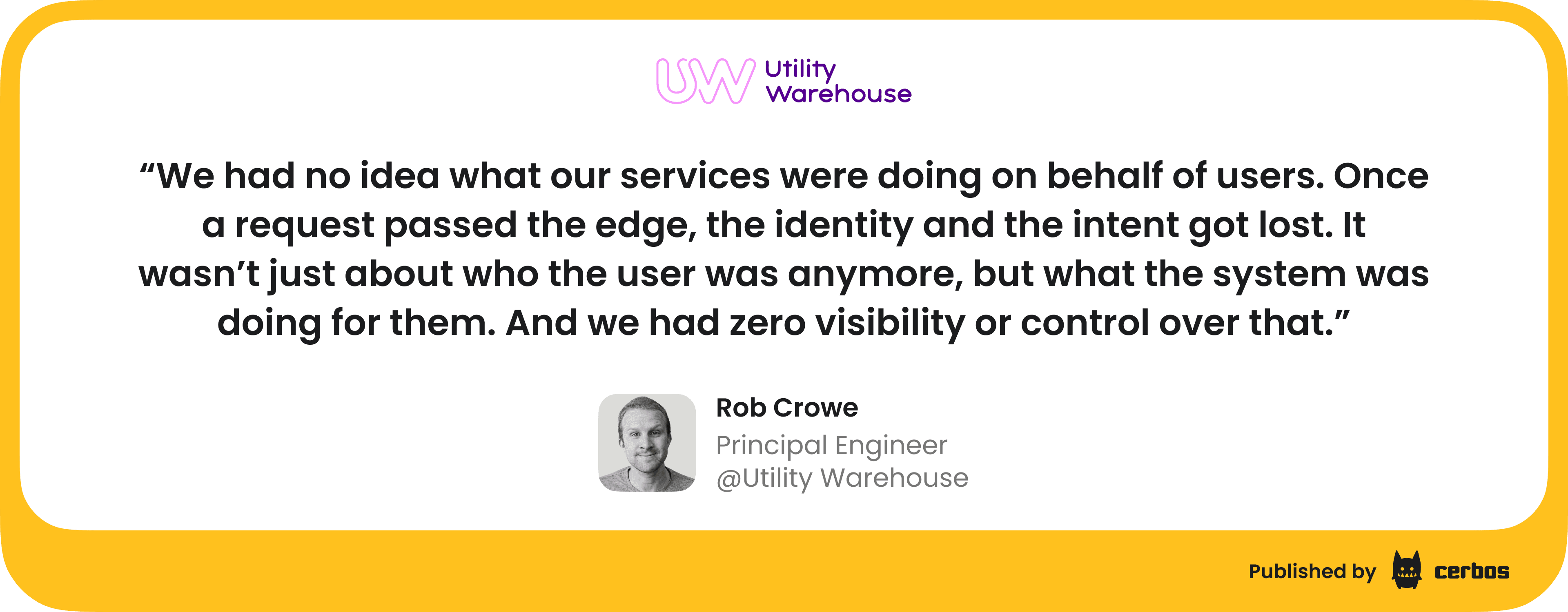
A few weeks ago, we hosted an MCP security webinar where we talked about AI risks related to Model Context Protocol and some horror stories 🙃. If you are following the IAM space, you probably heard of Asana’s multi-tenant bug that exposed task data, Supabase agents leaking full SQL tables through prompt injection, and Anthropic’s MCP Inspector bug that let attackers run code on developer machines. And all of it happened in the summer of 2025.
With their lack of security and growing abundance, NHIs have really become one of the riskiest assets inside your technical stack. In this article, I’ll walk through strategies to help you secure your NHIs and share insights we’ve heard directly from security leaders.
Note: This article is a part of a larger guide on securing Non-Human Identities. If you're interested in tackling NHIs & AI agent risks and choosing the right toolkit, you can get the full ebook here.
Non-human identities security strategy: a 6-step framework
Securing NHIs properly is not simple. It is a deliberate shift, from ad hoc NHI access control to intentional, risk-informed NHI governance that adapts as the organization evolves. That means aligning your architecture, operating model, and engineering priorities to support secure, scalable identity management across systems.
To help with that, we’ll walk through a set of practical strategies for securing NHIs. But first, let’s set a strong foundation on three rules:
-
Always treat humans and machines differently.
-
Establish areas of responsibility and work closely with cross-functional teams (security, IAM, engineering).
-
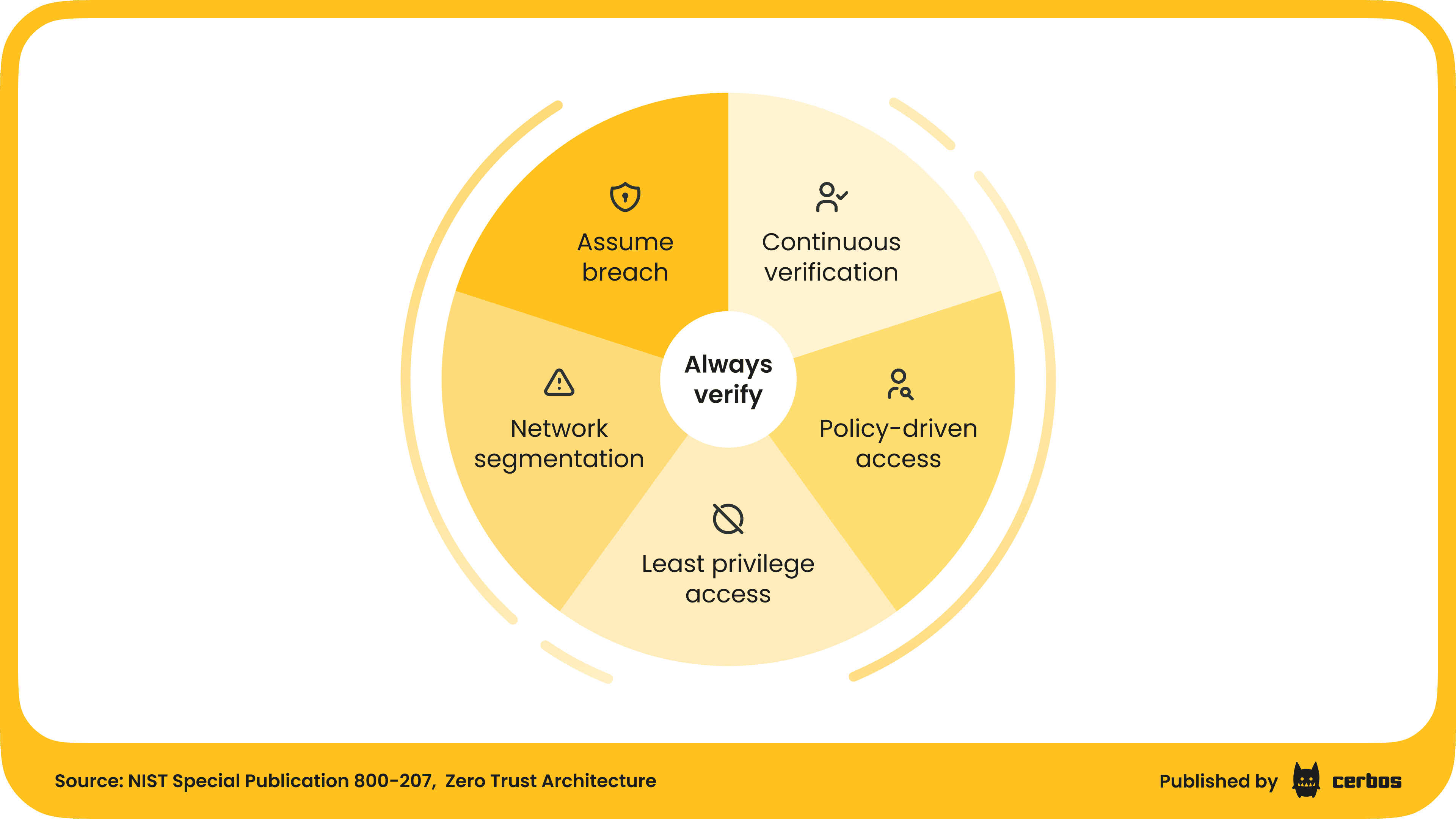
Follow the Zero Trust security model. Zero Trust is a set of security principles that define a design approach focused on eliminating implicit trust. These principles, based on NIST Special Publication 800-207 (NIST SP 800-207), include:
- Give the least privileged access possible
- Segment your network
- Always verify
- Assume breach
- Enforce access through centralized, policy-driven decisions.
👆With that foundation in place, you can build a structured, actionable NHI security strategy by following 6 key steps. Let’s unpack each of these steps to give you a better idea of what they include:
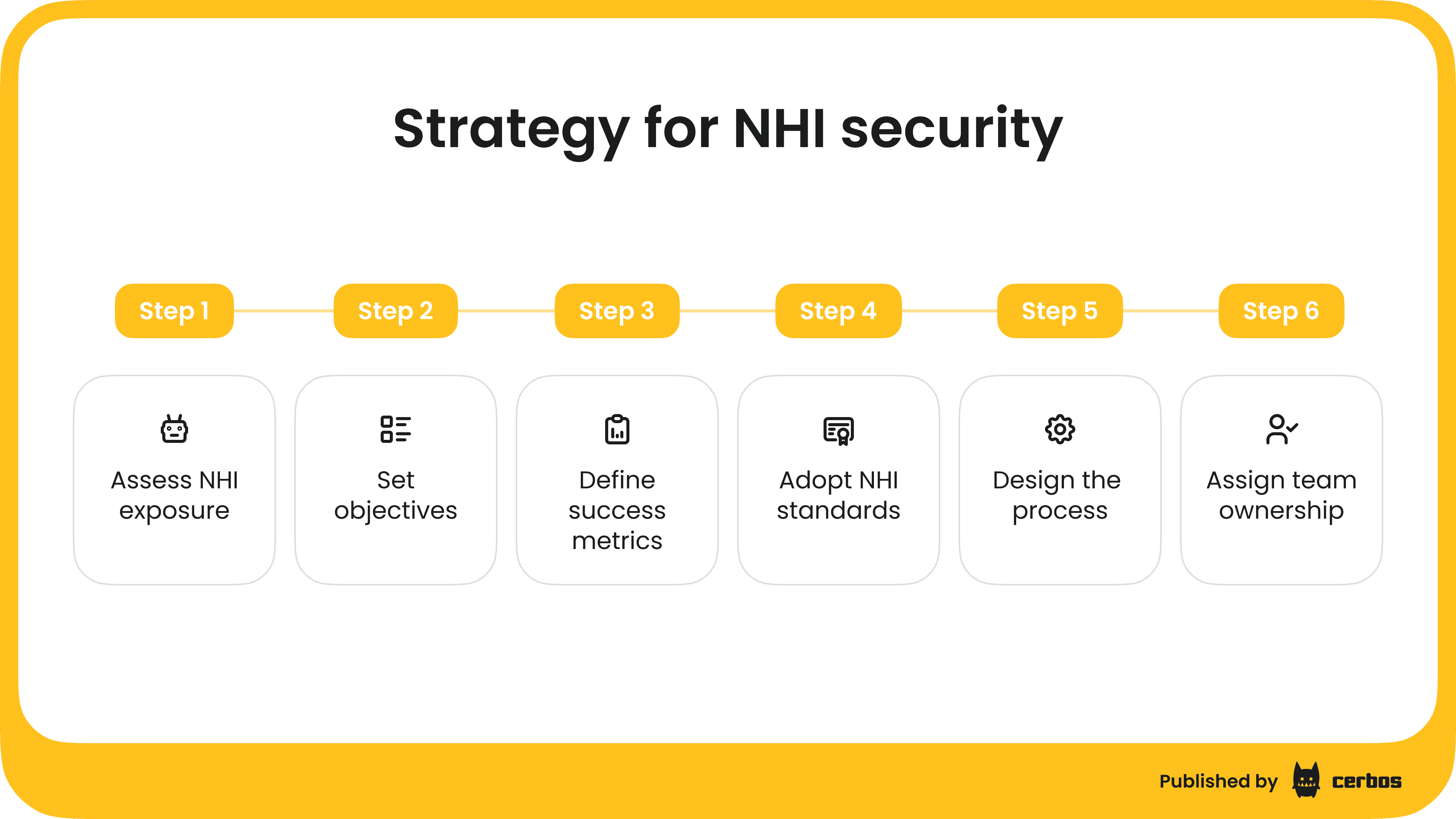
Step 1: Assess NHI exposure
A sound NHI security strategy begins with identifying and quantifying NHI-associated risks across your environment. To properly understand your exposure, you need to understand how NHIs are used in your organization:
- The roles they play
- The systems they access
- The data they touch
Once you understand your risk during your NHI discovery, you can define your objectives. But getting to that level of clarity is easier said than done.
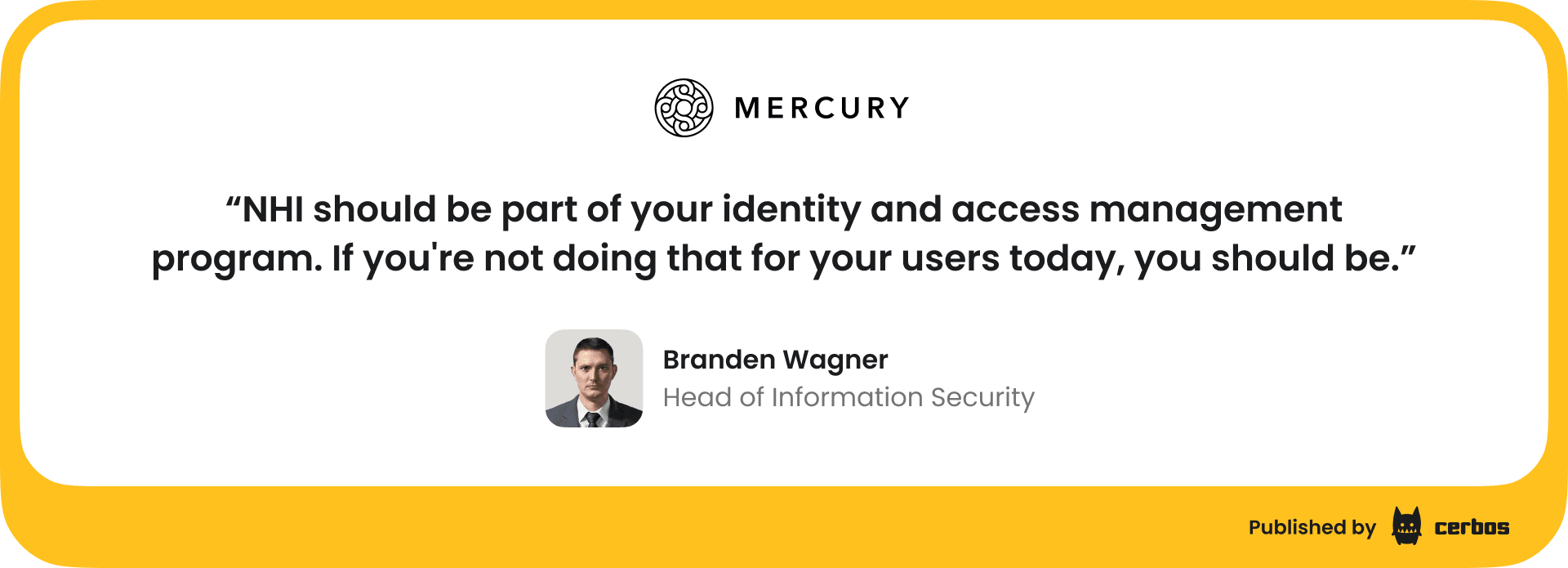
Many teams struggle to get a complete picture of what identities exist, what they have access to, and where they’re active. I loved the talk from Itzik Alvas, Entro Security CEO, on how this was an issue even at Microsoft: “The main problem we’re seeing in organizations, and the main problem we had at Microsoft is that usually organizations don’t really know how many non-human identities and secrets they have and where they are.”
So when you assess NHI exposure, do not limit it to service accounts and tokens in production. NHIs exist everywhere in your stack, from OAuth apps in the user domain to CI/CD secrets in development to AI agents. The development and AI domains are usually the riskiest, because credentials spread quickly and security practices are weaker. Looking at exposure by domain helps you see where controls will matter most!

Step 2: Set objectives
As you begin to set your NHI security objectives, base them on:
- Zero Trust principles
- Your use case and IAM programs
- Your compliance requirements
And remember to focus on outcomes that can be enforced through technical controls, not just written policies. You can set broad goals that cover all areas of NHIs, like Workload IAM, API access control, and workload federation. Alternatively, you can set more focused goals, like improving NHI permission management first.
This is where Cerbos Hub can help. Once objectives are defined, you need a way to translate them into policies and enforce them consistently across services, workloads, and AI agents. Cerbos Hub makes that possible by giving teams one place to create, test, and deploy policies, and then log every authorization decision for audit and compliance (sorry, for a bit of self-promotion 🙃). Now let’s move to the next step.
Step 3: Define success metrics for your NHI strategy
By defining clear metrics as part of your strategy, you build in feedback loops that allow you to track implementation.
For NHIs, these metrics can include:
- Percentage of NHIs with scoped, short-lived credentials
- Number of unused or orphaned service accounts detected and decommissioned
- Time-to-revoke for compromised or deprecated identities
- Credential rotation frequency and coverage
- Number of high-risk NHIs flagged for access outside approved scopes
These metrics let you iterate your NHI strategy based on real-world outcomes, not assumptions. The CyberArk 2025 report (PDF) found that 50% of surveyed organizations had a breach in the past year tied to compromised machine identities, most often through poorly scoped API keys, SSL/TLS certificates, and service account tokens. Tracking metrics like scoping, rotation, and time-to-revoke directly addresses those weak points and helps keep your organization out of that 50%.
Step 4: Adopt NHI standards
Standards provide technical scaffolding for your strategy. Adopting them upfront reduces integration complexity and improves your security posture over time. Your architecture should be supported by standards that promote portability and secure design by default. These are the standards we find most useful:
| Standard | Description | Benefits |
|---|---|---|
| SPIFFE | Secure identity framework for workloads; supports ephemeral identity via X.509 or JWT SVIDs | Enables cryptographic workload identities, short-lived credentials, and strong attestation |
| WIMSE (IETF) | Web Infrastructure Machine Security Ecosystem | Focuses on workload identity propagation, attestation, and fine-grained runtime authorization across clouds |
| SPICE (IETF) | Secure communication protocol for isolated compute environments | Supports secure, authenticated comms in multi-tenant and virtualized environments |
| OpenID Connect M2M | Extension of OIDC for machine-to-machine authentication | Supports interoperable and standards-based identity brokering between NHIs |
| FIDO Device Onboarding (FDO) | Secure, zero-touch onboarding of edge and IoT devices | Automates identity provisioning and ownership verification at the edge |
Choosing the standards now, before implementation, will give you the scaffolding needed to define which tools you need. (We cover tools in our ebook: Securing AI agents and non-human identities in the enterprise.)
Step 5: Design the process
Once you fully understand where your NHI security sits, and what your objectives are (and the standards you will rely on to guide you), you can map out how you are going to get there.
As you go through this process, you’ll define how NHIs are created, governed, rotated, monitored, and decommissioned across teams and environments. We find this example roadmap from Delinea really helpful in illustrating what this process can look like in real life. It breaks things down into clear, practical steps.
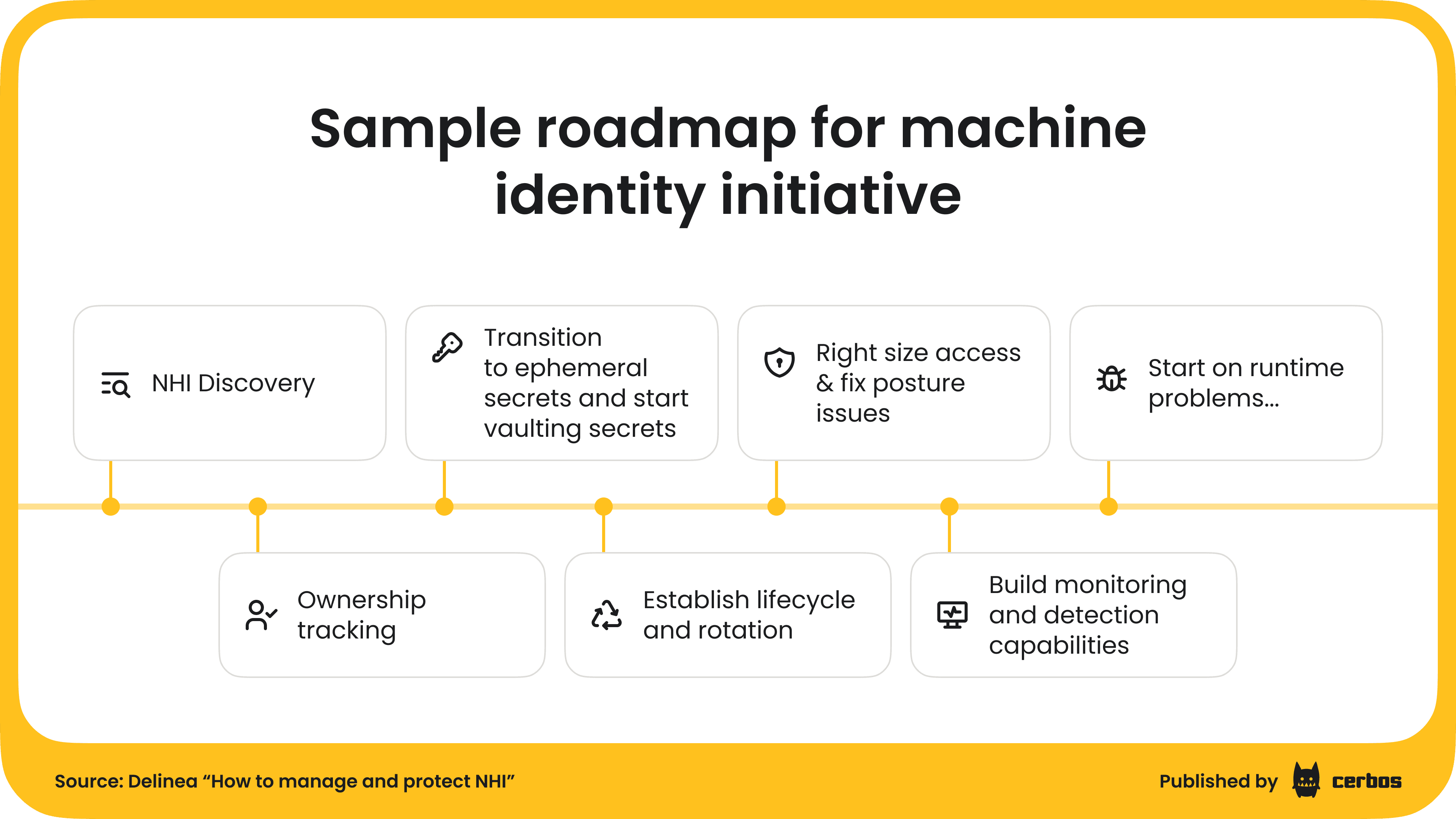
The ASP.NET machine key leak in early 2025 showed what happens when these basics are missing. Thousands of long-lived keys ended up in public repos, creating a path for remote code execution. A clear process for credential rotation, monitoring, and retirement would have caught and removed those keys before attackers could exploit them!
Step 6: Assign team ownership
With your operational practices mapped out, the next step is to map the process over your team. This way, you ensure that every step of implementation is owned by a responsible team member (or team).
Typically, that will look something like this:
- Security teams define risk models, enforce controls, and oversee auditability.
- IAM teams manage access policy, identity issuance, and lifecycle orchestration.
- Platform/DevOps teams implement tooling, rotate secrets, and enforce runtime controls.
- Application teams consume secure identity patterns and surface misuse or gaps.
As Felix Gaehtgens, VP Analyst at Gartner mentioned in one of KuppingerCole's video series: “IAM teams are basically missing in action when it comes to machine IAM. This is creating this massive leadership vacuum.” That vacuum often leaves security and engineering teams to pick up the slack, making clear ownership even more important.
So, the NHI security responsibilities will depend on your company and who historically owned security. It’s also important to remember that security is a team sport, requiring cross-functional collaboration. I will leave here a quote which came up on one of my expert calls with CISO, and I truly love this opinion:

Once you have the high-level NHI security strategy in place, the next step is to make it work in practice. A strategy gives direction, but principles shape how teams actually secure and manage NHIs day to day.
In part two, we’ll cover the practical principles that put NHI and AI security into action. Our co-founder, Emre Baran, will take you through them next.
TLDR or key takeaways:
-
Non-human identities already outnumber human accounts in most environments and are often over-privileged or invisible. This creates one of the biggest security risks in your stack. To overcome this, follow strategies for securing NHIs (aka your NHI security strategy).
-
Start with exposure mapping. Most orgs don’t even know how many NHIs and secrets they have or where they are, which makes blind spots inevitable.
-
Set objectives that can be enforced with technical controls. Focus on least privilege, Zero Trust, and aligning goals with compliance and IAM requirements.
-
Define success metrics to track progress. Metrics like credential rotation, time-to-revoke, and orphaned account cleanup directly address the weaknesses behind 50% of recent breaches (CyberArk 2025).
-
Adopt standards like SPIFFE, OIDC M2M, and FIDO Device Onboarding to enforce portable, cryptographic identity management across clouds and workloads.
-
Design the process for lifecycle management: creation, governance, rotation, monitoring, and retirement of NHIs.
-
Assign clear ownership across security, IAM, DevOps, and application teams. Gartner warns IAM is “missing in action” on machine identities, leaving a leadership vacuum that must be closed. Use tools like Cerbos Hub to manage access for humans and machines.
FAQ
Book a free Policy Workshop to discuss your requirements and get your first policy written by the Cerbos team
Related Articles
Subscribe to our newsletter
Join thousands of developers | Features and updates | 1x per month | No spam, just goodies.






